Secure your app login with real-time authentication


Authentication can run automatically without requiring any action from the user.

Development more efficient as the authentication process occurs through carrier network.

Minimizes the risk of cyber attacks and account takeover for users.

Provides the possibility for integration with other authentication solutions
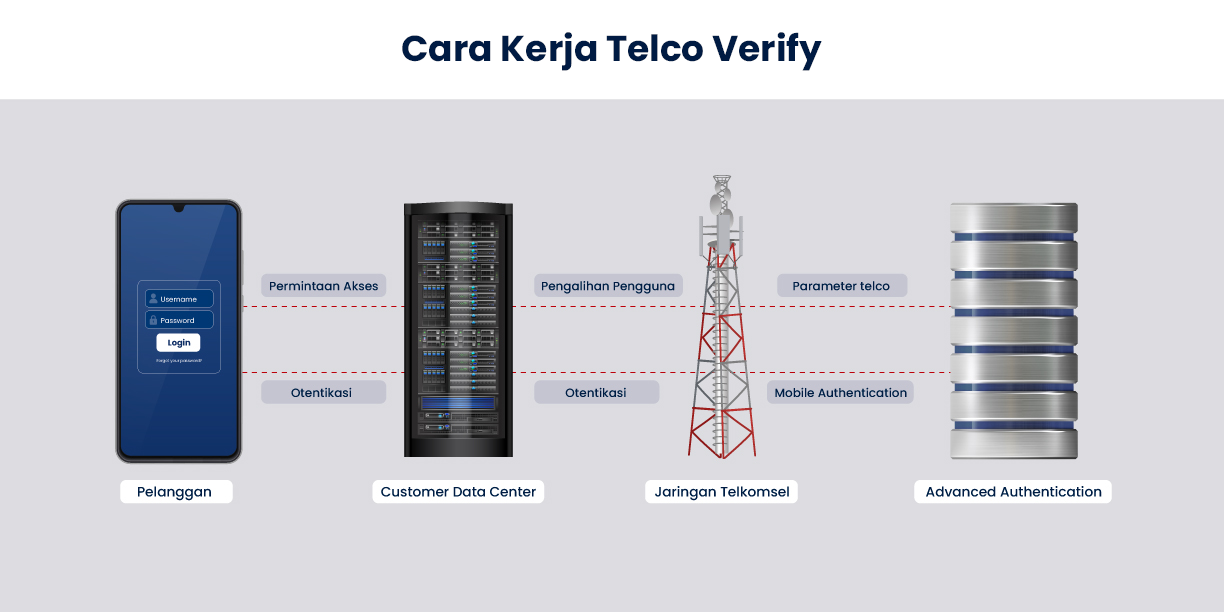

This method can still be used even if the user is using WiFi or even operators other than Telkomsel.
Majority tend to use mobile phones, but it's possible to use other media such as QR codes.
The connection will automatically switch to cellular network for authentication. As a result, the authentication process will continue running when the user is switched to the WiFi network.
This method does not require users to access a URL, unlike OTP methods that involve users in entering a code. This solution will directly authenticate the provided URL.
User is required to have a data package or credit to be verified on the mobile network
Telco Verify is an authentication solution with the latest secure technology, that is secure against cyber threats, as users do not need to input any verification code in the application.

Tell us your business needs.

We will plan a solution according to your needs and provide a trial.

Make cooperation agreements for commercial implementation of solutions.

Solution implemented to your application.
![]()

Mobile Endpoint Protection
Address threats and analyze viruses on devices, equipped with Machine Learning.

Mobile Device Management
Maintain the security of employee devices that can be access at any time.

Telkomsel Guard
Device protection application from cyber attacks with Machine Learning.

Network Security
Network protection without reducing performance through Telkomsel premises.
Our site uses cookies to improve your experience. By continuing, you have agreed to the applicable Terms & Conditions and Privacy Policy.
© PT TELEKOMUNIKASI SELULAR, 2025